What Is Peer-to-Peer (P2P) Protocol? Types Of Peer-to-Peer Protocol?
Category: NETWORKING | 20th July 2025, Sunday
A Peer-to-Peer (P2P) Protocol Is A Communication Model Where Each Participant (called A peer) Acts Both As A client And A Server. This Means That Every Node Can initiate Or Complete Data Exchanges, Without Relying On A Centralized Server.
Key Characteristics:
-
Decentralization:
-
No Central Authority Is Needed To Manage The Network.
-
Peers Connect And Share Resources Directly With Each Other.
-
-
Equal Role Of Peers:
-
Each Node (computer Or Device) Can Both Request And Provide Data Or Services.
-
Unlike Client-server Models, Peers Are Symmetrical.
-
-
Scalability:
-
P2P Networks Can Easily Scale As More Peers Join The Network.
-
Each New Peer Adds Resources Rather Than Consuming Them Alone.
-
-
Resource Sharing:
-
Bandwidth, Processing Power, And Storage Can Be Shared Among Peers.
-
Examples Of P2P Protocols:
| Protocol | Use Case |
|---|---|
| BitTorrent | File Sharing (downloads Are Divided Among Peers) |
| Gnutella | Distributed Search And File Sharing |
| IPFS (InterPlanetary File System) | Decentralized Web And File System |
| Blockchain (e.g., Bitcoin Protocol) | Secure Financial Transactions Over Decentralized Networks |
Working Of P2P Protocol (Simple Steps):
-
Peer Discovery:
-
Each Node Finds Other Peers In The Network Using Trackers Or DHT (Distributed Hash Tables).
-
-
Handshake:
-
Two Peers Authenticate And Agree To Communicate.
-
-
Data Exchange:
-
Peers Exchange Data Chunks Or Services.
-
Redundancy And Replication Ensure Data Integrity.
-
-
Disconnection And Reconnection:
-
Peers Can Freely Leave Or Join The Network At Any Time.
-
Advantages:
-
Fault Tolerant: No Single Point Of Failure.
-
Efficient Resource Usage: Shared Resources Reduce Bottlenecks.
-
Cost-Effective: No Need For Central Servers.
Disadvantages:
-
Security Risks: Harder To Control Or Monitor Malicious Activity.
-
Data Integrity: Ensuring Reliable Data From Unknown Peers Is Challenging.
-
Complex Discovery Mechanisms: Maintaining Connectivity Requires Advanced Algorithms.
Applications Of P2P Protocols:
-
File Sharing Systems (e.g., BitTorrent)
-
Cryptocurrency (e.g., Bitcoin, Ethereum)
-
Decentralized Cloud Storage (e.g., Filecoin)
-
VoIP Services (e.g., Skype – Early Versions)
Peer-to-Peer Protocols Offer A robust, Decentralized, And Scalable Alternative To Traditional Client-server Models. For PG Students, Understanding P2P Is Essential In Areas Like distributed Systems, blockchain, And decentralized Computing.
Who Developed The Peer-to-Peer (P2P) Protocol?
1. No Single Creator – It's An Evolving Concept:
The Peer-to-Peer (P2P) Protocol Is Not A Single Protocol Developed By One Person Or Organization. Instead, It's A design Philosophy Or communication Model That Has Evolved Over Decades. Many Researchers, Companies, And Open-source Communities Have developed Various P2P Protocols To Suit Different Applications.
Historical Milestones & Key Contributors:
| Time Period | Contribution | Developers/Organizations |
| 1960s-1980s | Early Concepts Of Distributed Computing (precursors To P2P) | ARPANET, Academic Researchers |
| 1999 | Napster – One Of The First Mainstream P2P File-sharing Apps (hybrid P2P) | Shawn Fanning & Sean Parker |
| 2000 | Gnutella Protocol – Fully Decentralized P2P Protocol | Nullsoft (a Subsidiary Of AOL) |
| 2001 | BitTorrent Protocol – Efficient File Sharing Using Peer Swarming | Bram Cohen |
| 2008 | Bitcoin (Blockchain-based P2P Protocol) | Satoshi Nakamoto (pseudonymous) |
| 2015+ | IPFS & Filecoin – P2P Web And Storage | Protocol Labs (Juan Benet) |
Current Developers And Maintainers:
-
Open-source Communities Contribute To P2P Libraries And Protocols (e.g., BitTorrent, Libp2p).
-
Academic Researchers Explore New Designs (e.g., Scalable P2P Overlays, DHT Algorithms).
-
Tech Companies Like Microsoft, Google (WebRTC), And Protocol Labs (IPFS) Innovate In P2P-based Applications.
-
Blockchain Developers (Ethereum, Bitcoin Core) Use And Extend P2P Networking In Decentralized Finance.
P2P Protocol Development Is A collective And Ongoing Effort Involving Computer Scientists, Open-source Communities, And Innovators. No Single Individual Owns The "P2P Protocol," But Many Have Contributed specific P2P Technologies And Standards That Are Widely Used Today.
Types Of Peer-to-Peer (P2P) Protocols
Peer-to-peer (P2P) Protocols Can Be classified Based On Their Architecture And Functionality. Understanding These Types Helps In Designing Efficient Decentralized Systems Like File Sharing, Blockchain, And Content Distribution.
1. Based On Network Architecture:
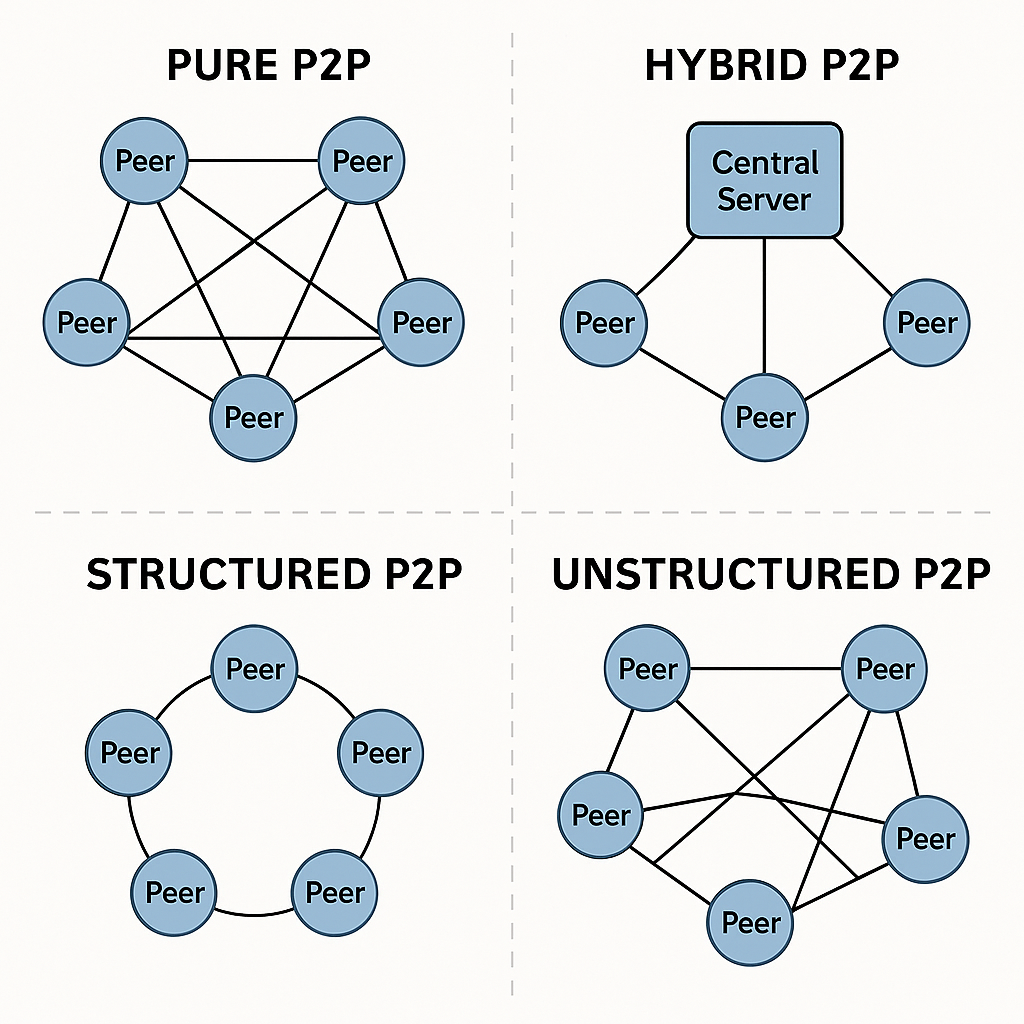
A. Pure P2P Protocol
-
Definition: No Centralized Control; All Nodes Are Equal.
-
How It Works: Each Peer Can Search, Upload, And Download Data Without A Central Index.
-
Example: Gnutella (v0)
Pros:
-
Fully Decentralized
-
High Fault Tolerance
Cons:
-
High Search Latency
-
Difficult To Manage Routing
B. Hybrid P2P Protocol
-
Definition: Combines Centralized Servers For Some Tasks (e.g., Peer Discovery) And P2P For Data Transfer.
-
Example: Napster (centralized Index, Peer-based File Transfer)
Pros:
-
Faster Search
-
Easier To Manage
Cons:
-
Central Point Of Failure
-
Less Decentralized
C. Structured P2P Protocol
-
Definition: Uses A Defined Structure (like A Distributed Hash Table - DHT) To Organize Peers And Content.
-
Example: Chord, Kademlia (used In BitTorrent)
Pros:
-
Efficient Data Lookup (O(log N))
-
Scalable
Cons:
-
Complex Algorithms
-
May Need Stabilization Protocols
D. Unstructured P2P Protocol
-
Definition: No Specific Rules To Place Or Search Data. Peers Randomly Connect.
-
Example: Freenet, early Gnutella
Pros:
-
Simple And Robust
-
Good For Dynamic Networks
Cons:
-
Inefficient Search (flooding)
-
High Bandwidth Usage
E. Super-peer P2P Protocol
-
Definition: Some Peers Act As super-nodes That Index Content For Other Peers.
-
Example: Skype (early Versions), Kazaa
Pros:
-
Balanced Architecture
-
Reduced Search Time
Cons:
-
Super-nodes Can Be Overloaded
-
Partial Centralization
2. Based On Application Use:
| Type | Purpose | Example |
| File-sharing P2P | Sharing Large Files Between Peers | BitTorrent |
| Streaming P2P | Live Audio/video Distribution | PPLive, SopCast |
| lockchain-based P2P | Distributed Ledger And Transactions | Bitcoin, Ethereum |
| Collaborative P2P | Sharing Resources Like CPU/storage | BOINC (grid Computing) |
| Anonymous P2P | Privacy-focused Communication | Tor, I2P |
Summary Table
| Protocol Type | Structure | Example | Key Feature |
| Pure P2P | Decentralized | Gnutella | All Nodes Equal |
| Hybrid P2P | Centralized + P2P | Napster | Central Index |
| Structured P2P | DHT-based | Chord, Kademlia | Fast Lookup |
| Unstructured P2P | Random Connections | Freenet | Simple Design |
| Super-peer P2P | Hierarchical | Skype | Faster Routing |
Conclusion:
The type Of P2P Protocol Used Depends On The application's Need For Decentralization, Scalability, Fault Tolerance, And Performance.
Tags:
Peer-to-Peer (P2P) Protocol, P2P, Peer-to-Peer Protocol
